You can configure multiple instances of various SSO providers within your organization, offering unmatched flexibility. Multiple SSOs are advantageous if different teams within your organization rely on distinct authentication systems from providers like Okta, Google, Microsoft Entra ID, OneLogin, and more.
Configuring multiple instances of the different SSO providers streamlines management and ensures a smooth login experience across your preferred identity platform.
Note
This article uses Okta and OneLogin, but the steps are identical to those of other providers. The only difference is the mapping of the metadata details.
Adding Okta as the First SSO Provider
Ensure that your Okta Metadata details are ready! If you already have it, let’s add it!
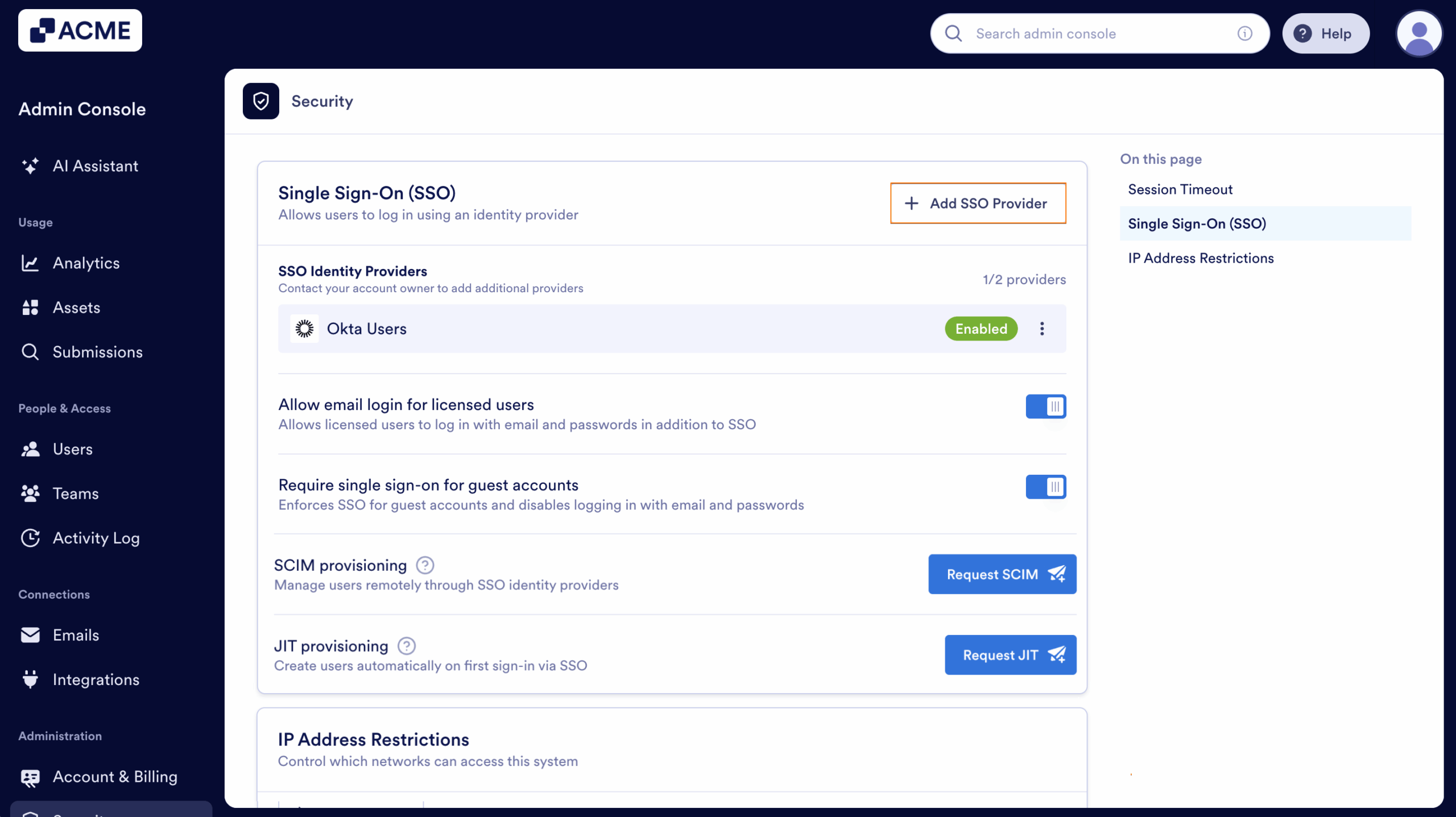
- In the Admin Console, in the left menu click on Security.
- Under Single Sign-On (SSO), select Add SSO Provider.
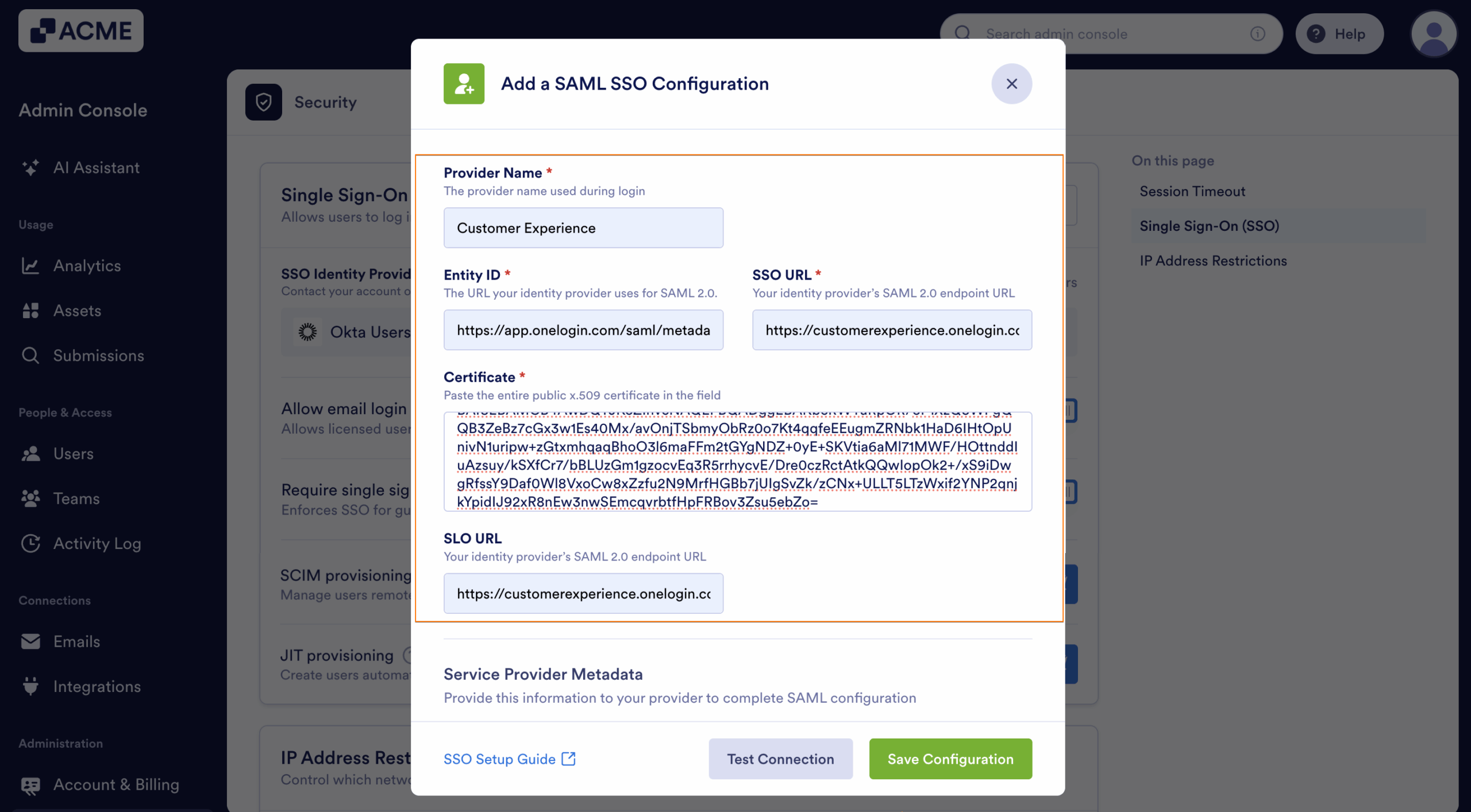
- Select Configure Manually.
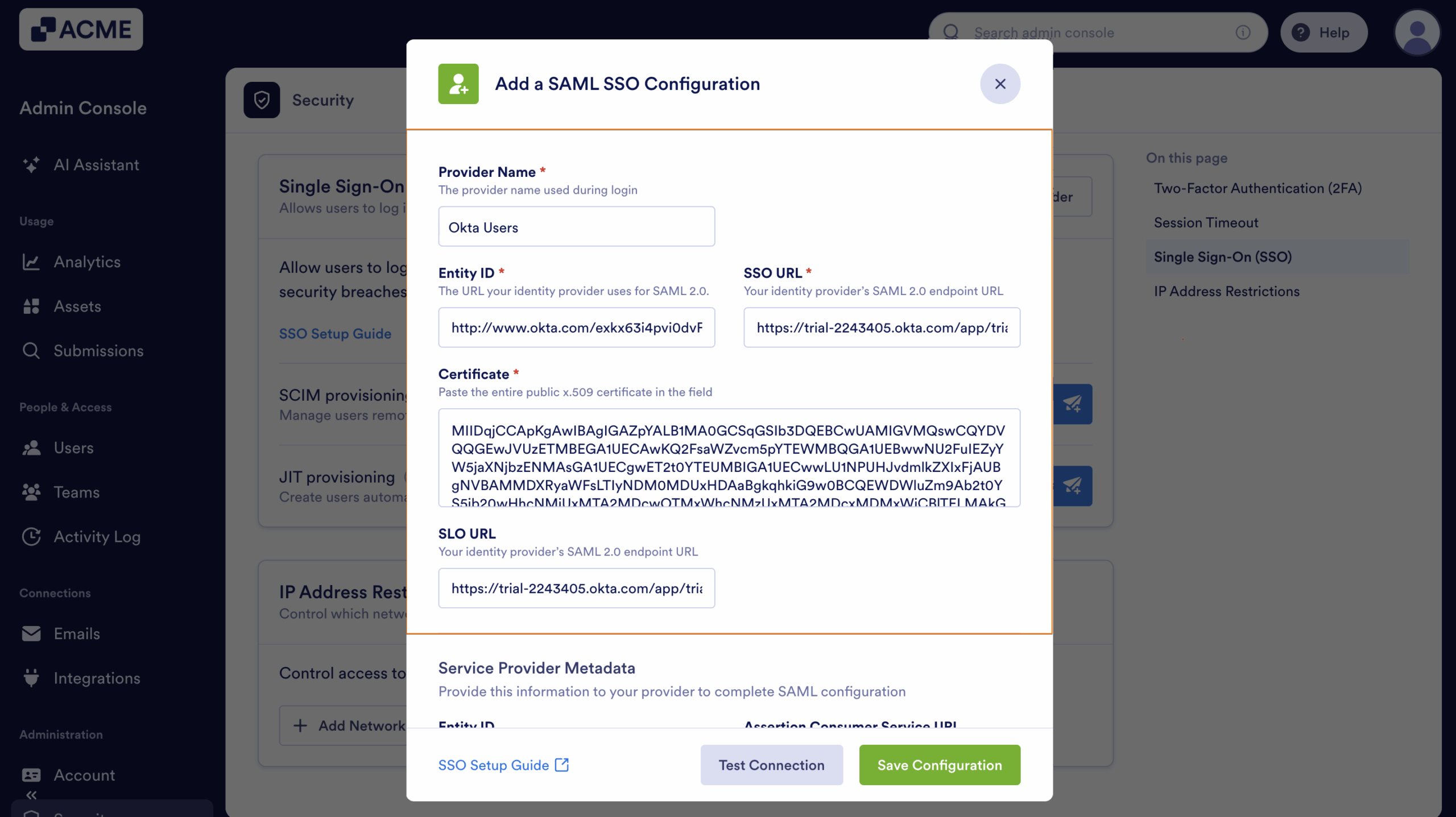
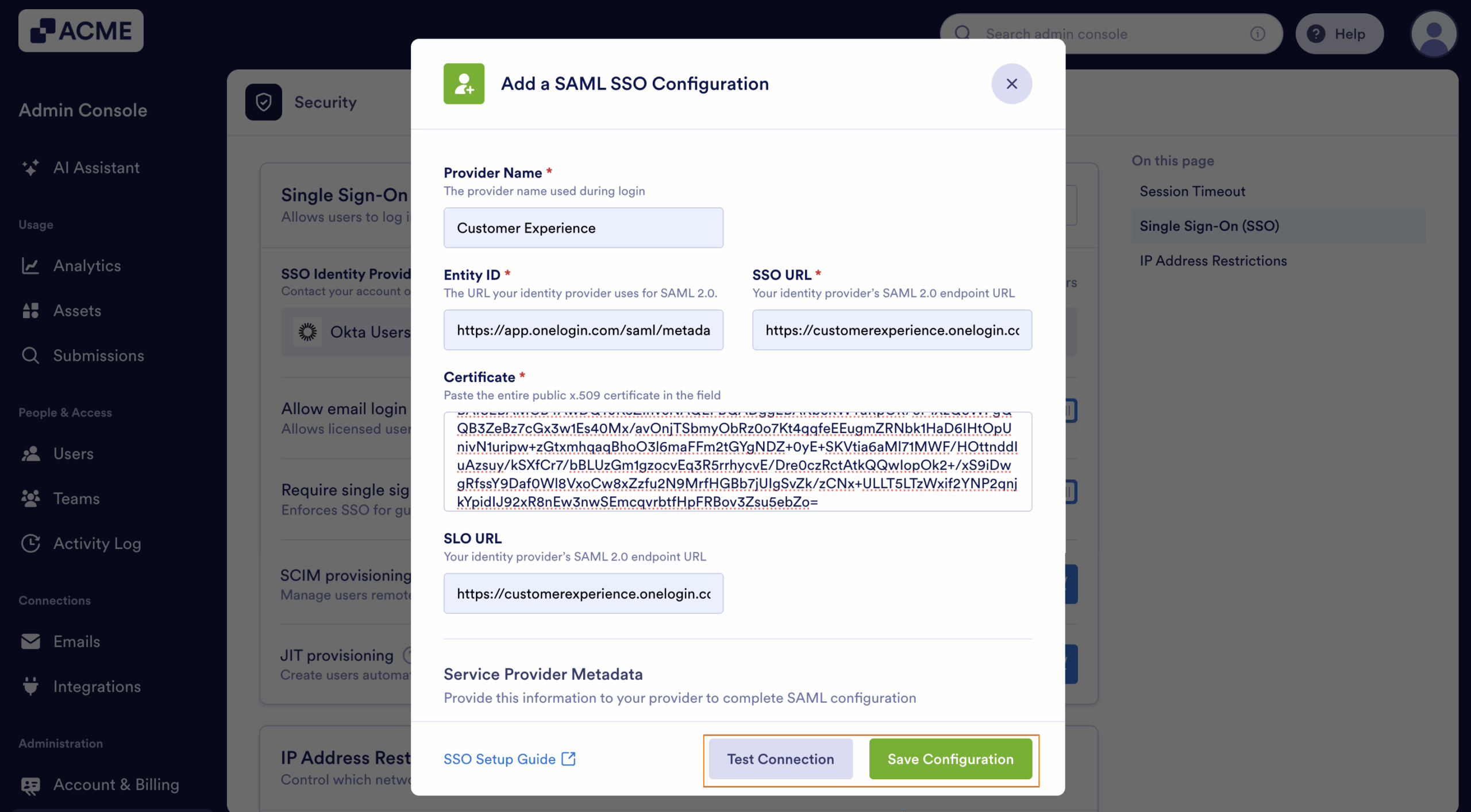
- Edit and map the following SAML SSO Configuration:
- Provider Name — Enter the name of the provider. You can input a more personalized name here for identification purposes.
- Entity ID — Input the Issuer URL from Okta.
- SSO URL — Paste the Sign on URL.
- Certificate — Your Signing Certificate from Okta.
- SLO URL — Paste the Sign out URL.
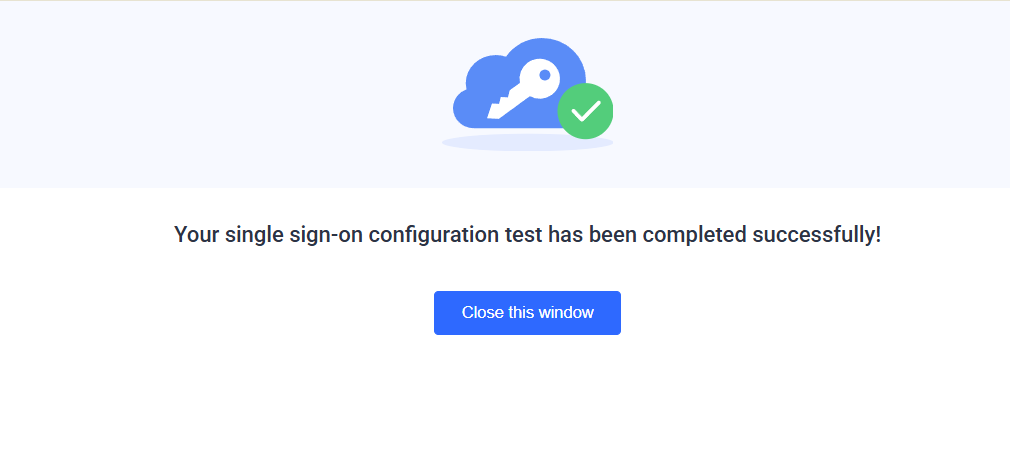
- Click the Test Connection to ensure that your SSO is working. If it’s working, you should receive the following message in the popup window:
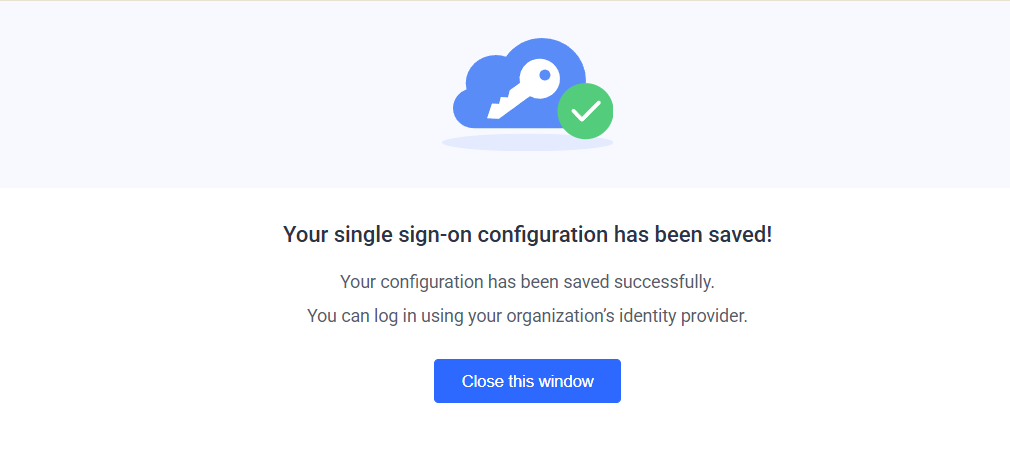
- Finally, click the Save button to complete the configuration. You’ll get the following confirmation message. Close the window to see your saved SSO configuration.
See also:
Adding OneLogin as the Second SSO Provider
Adding OneLoging will follow the same configuration as adding Okta. To add OneLogin as the second SSO
- Click the New SAML SSO Provider button, which is still in the Single Sign-On section.
- Enter and map the following metadata details from your OneLogin SAML application:
- Provider Name — Enter the name you want.
- Entity ID — Use your OneLogin SAML Entity ID.
- SSO URL — Use your OneLogin SAML SSO URL.
- Certificate — Use your OneLogin SAML Certificate.
- Click the Test Connection button to confirm if your configuration works. If it works, click the Save button to complete the integration and save it to your list of SSO providers.
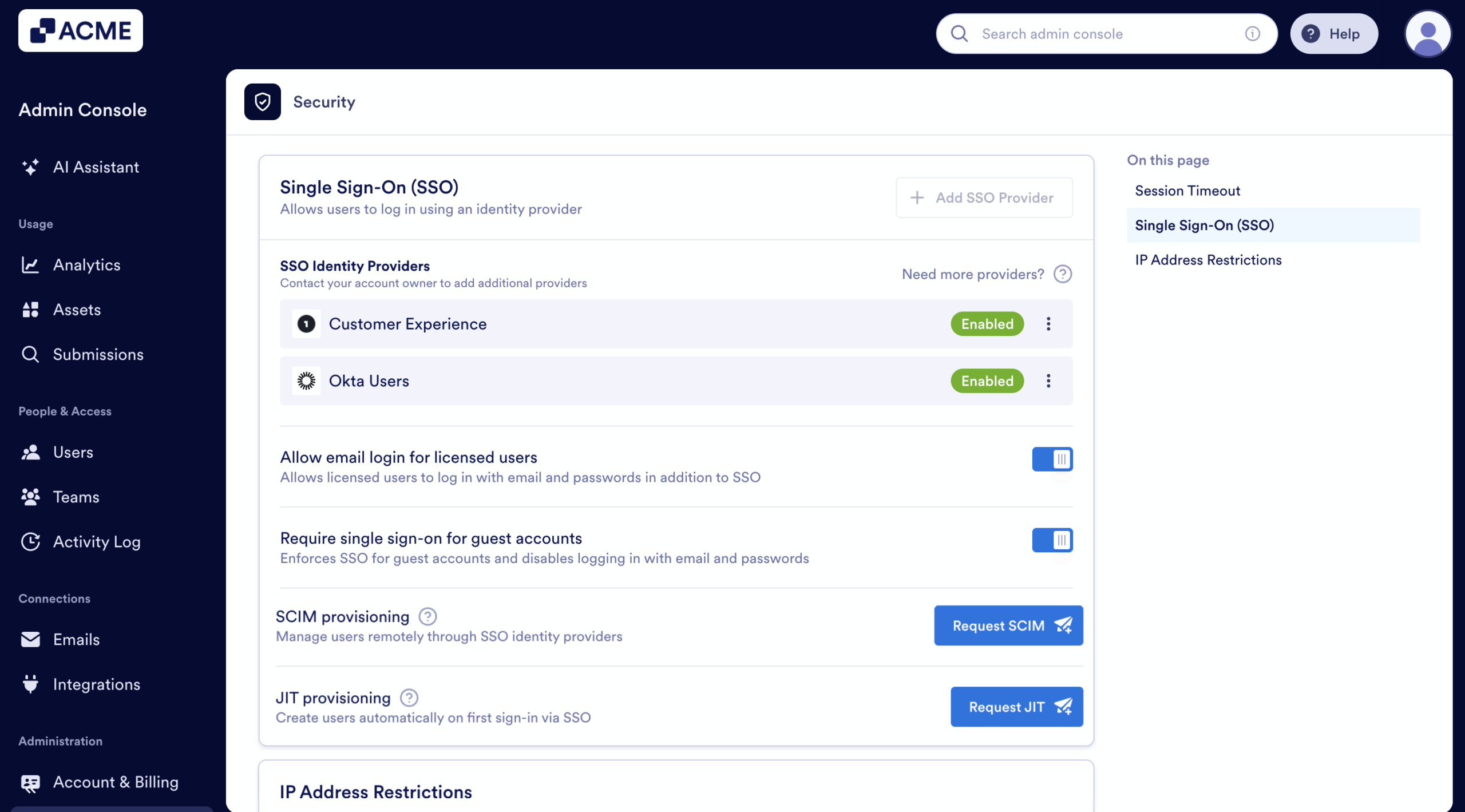
After adding, you’ll see all of the SSO providers listed on the SSO Settings section of your organization. Here’s an example:
See also: How to Set Up OneLogin SSO in Your Organization.
Managing Single Sign-On Configurations
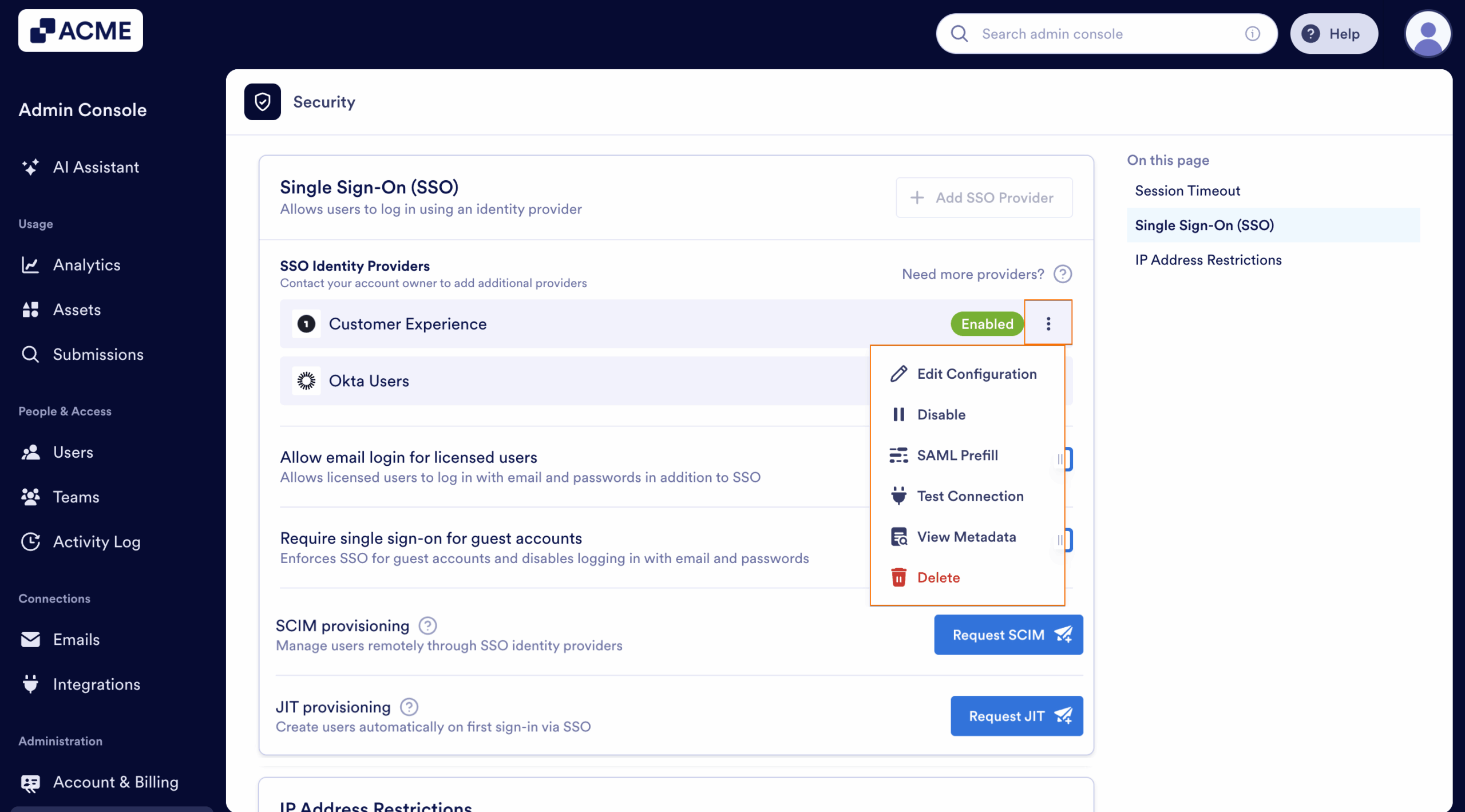
On each saved SSO configuration, click on the Menu (three-doted vertical icon) to manage them. You can edit the configuration, test the connection, and delete it from the list.
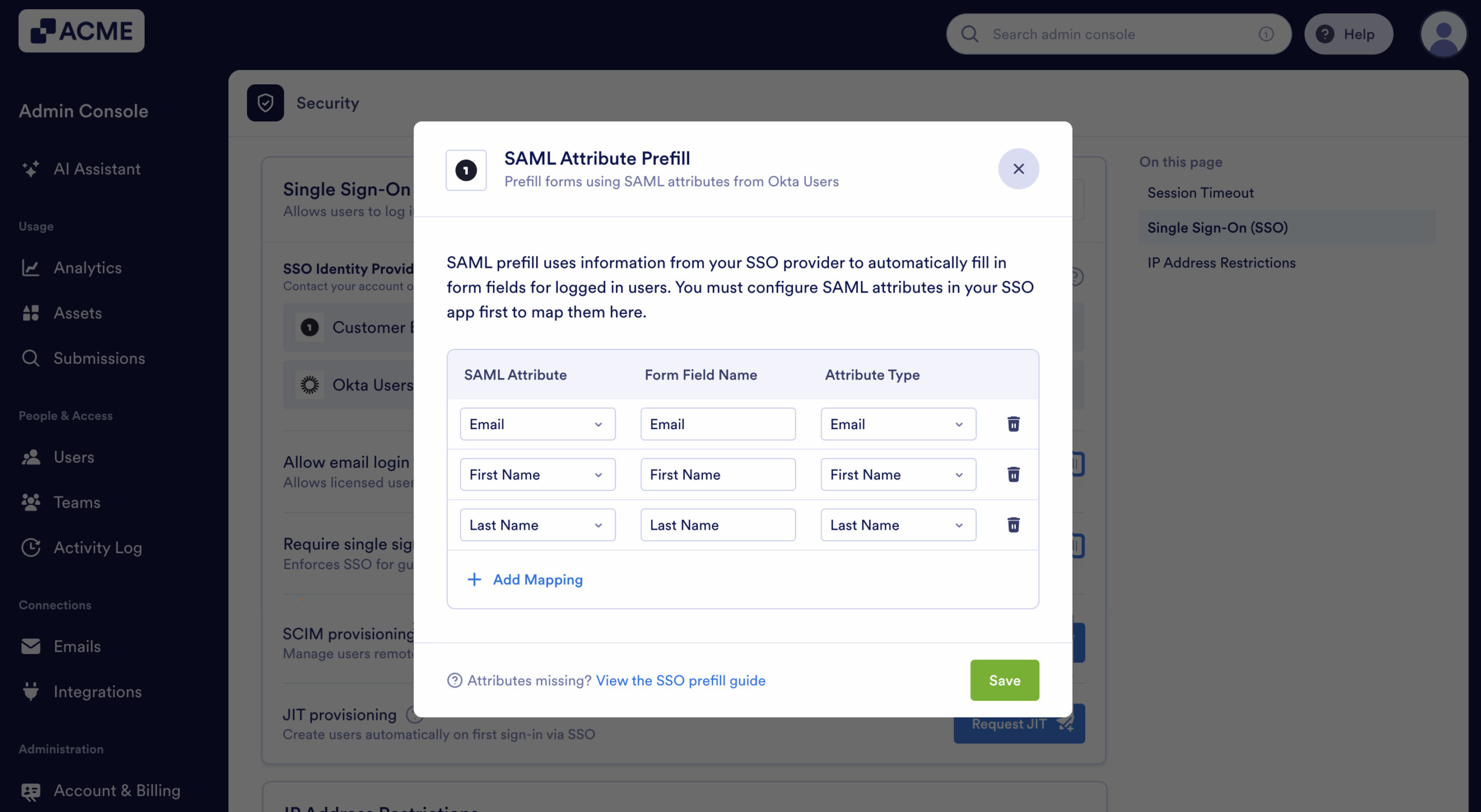
You can also configure the SAML Prefill of your SSO configurations. Click on the SAML Prefill button to set it up.
Logging In to Your Server with Multiple SSO
When logging in, you should see all of the SSO instances you’ve added to your Jotform Enterprise server. Here’s how the login screen looks:
As you can see, they’re both labeled as Okta and OneLogin, both based on the SSO configurations.
If you’re looking for our general information related to SSO integration, visit How to Enable SSO Integration in Your Organization to learn more.

Send Comment: